I have issues connecting to a open vpn server I’m running myself.
I can connect frim both a linux PC and an embedded device running linux/mips and all connections are routed through the vpn.
I copied the credentials to my SfOS phone.
After the connection was established, all traffic is routed through the vpn as well on my pc as on my embedded device.
The vpn is connecting from my jolla as well.
However, traffic is not routed through the vpn on my jolla, even when i invoke openvpn manually using exactely the same .ovpn config file.
I don’t get it.
Thanks you.
@Inte how do you test the route? I’d use traceroute and ip -r to find out the current configuration. Further, the output of the VPN daemon is usually very helpful with debugging. A stripped configuration file (anonymized and cryptographic details removed) could also help others to help you.
Maybe something like
push "redirect-gateway def1"
in your server.conf might help.
btw: What is your reason to use secure fish net? There is native support for openvpn in SFOS now.
I’m not using secure fishnet but the native implementation.
And, as I explained before, I also tried invoking openvpn from the command line using exactely the same configuration file as on my linux desktop.
I think I included some push route/gateway option in the server config, and I currently don’t dare to alter it remotely since fixing it (if the server fails) remotely is not possible. Will try when back home.
Can I also set the new default route manually? I tried both, command line and the advanced options tab of sfos but couldn’t figure out how. It doesn’t appear to work when configuring the same routes as on my desktop.
what is your command to change routes? what are your routes (route -n)?
You don’t have to change the server configuration. Put this into the client configuration, and you should be set:
If you, like me, don’t want all traffic to be routed via the VPN tunnel, this will not be a proper solution, though.
Although my OpenVPN connections already all work fine I tried
redirect-gateway def1
in a variant of my openvpn.conf. With and without that line all traffic even from Fennec (Android) was rooted through the VPN.
So I had a closer look at my server.conf.
I -as the original poster- do want all traffic to go through the vpn.
The lines responsible for the rooting and network setting are
push “route 192.168.96.0 255.255.255.0”
push “redirect-gateway def1 bypass-dhcp”
push “dhcp-option DNS 192.168.96.1”
192.168.96.0/24 is my home network and the DHCPD runs at 192.168.96.1. Local name resolution works fine and and traffic is routed as intended.
Indeed, if you push a default gateway with a OpenVPN server configuration, then you don’t need to set that in your client configuration. Anyway, we still don’t know what’s missing with @Inte’s setup.
But we sure made some nices suggestions to fix the problem from both sides. 
Weren’t there problems with Android Apps ignoring the VPN in former SFOS-Versions? That seems to be fixed at least for https.
Hey.
sorry for the late reply.
I have put the redirect-gateway line in my client config and now the traffic is indeed routed through the vpn. Thank you very much.
Is there a way to add this config line to the sailfish vpn-gui (maybe even manually through altering configfiles?).
I really don’t understand why those configs work on my other devices without this line, but well, fair enough.
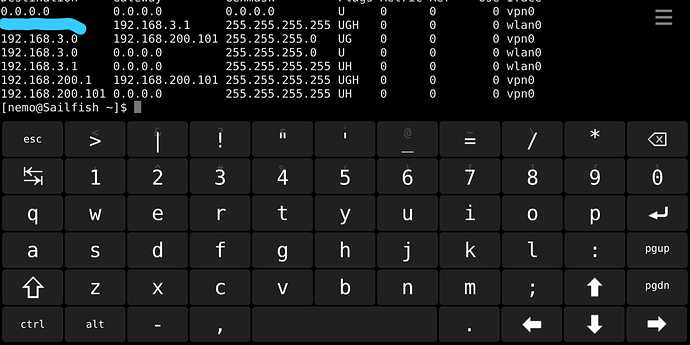
I just realized a difference in the routing table when connecting through the sailfish-gui vs connecting by invoking openvpn from the command line (both using the same .ovpn file):Both routing tables are identical, except for the routing setup through the gui tries to setup and route all traffic through “vpn0”, while when invoking from the command line, a tun0 device is created and all traffic and routes are configured for tun0.While routing through vpn0 does not work (the traffic to networks outside the vpn is simply blocked), all works well through the tun0 device.Why is the gui utilizing vpn0 in favor to tun0, and how to fix this?
To ask in brief:
What is the difference between tun0 and vpn0?
And why is the tun0 device used when invoking openvpn from the command line, but vpn0 when invoking through the GUI? As described above, while tun0 works this doesn’t appear to be the case for vpn0?
vpn0 is presumably just an ifrenamed interface name for tun0, or more precisely, as ifrename is unavailable on stock SFOS, it’s renamed by ip link set tun0 name vpn0. It shouldn’t be functionally different.
I really don’t get the point.
The tun0 config works while the vpn0 config doesn’t.
Edit:
Whoops.
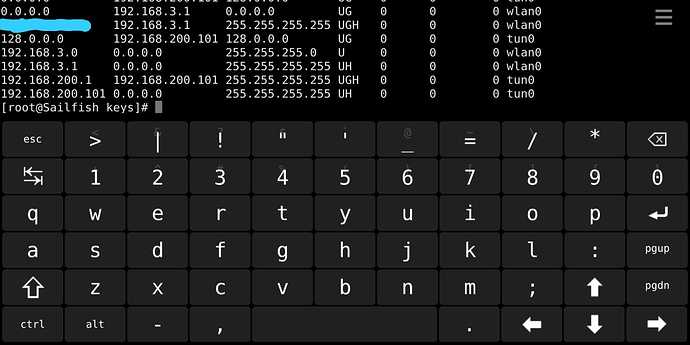
I just realized I’m missing the 128.0.0.0 route. How do I add that one? And what does it do at all?
As I said before, I’ve imported the same .ovpn file into the gui that works flawlessly from the command line…
It sets a route via tun0 for all target addresses starting with bit 1 set, which replaces half of the default route by being more specific. There should be a corresponding route for the other half, those with leading zeroes. This is a clever way of overriding a default route without altering it. The additional routes can be removed later, thus restoring the previous default route.
All right , thanks for the explaination.
So it seems the sfos gui is not setting the routes properly?
Is this a bug or am I doing something wrong?
The SFOS GUI implementation replaces the default route, it does not override it.
On the other hand, in the GUI case (top image), you see a route to 0.0.0.0 without mask via vpn0 without a gateway (gw is 0.0.0.0 without the G flag). This is odd. It probably breaks any traffic except to those addresses having a more specific rule; or in other words, it may break the default route.
Thank you very much.
Yes, it breaks any traffic except for that routed to the connected vpn.
I played around a bit a figured out that this route is beeing set by the vpn-GUI when checking the standard-gateway option.
I have then unchecked this option and set two additional routes manually, to 0.0.0.0 and to 128.0.0.0 as in the command-line vpn.
Now I’m kind of half way through! 
All traffic is indeed now routed through the vpn! At least, when I’m on a standard ipv4 internet connection.
When using an ipv6 connection (e.g. my wifi connection) the ipv6 adress of my phone is still visible. Is there any way to hide my ipv6 address/ mask it with my ipv4 address?
Btw the ipv6 ip is also visible when connected from the command line.
OpenVPN servers can be configured to be gateways for both IPv4 and IPv6 traffic at the same time, even default gateways. I set up some dual protocol gateways. They can even be set up to offer this service via IPv4 or IPv6 on the tunnel layer and tunnel IPv4 and IPv6, so whatever you have available, it’ll just work.
Client-side, it looks like this:
<connection>
remote 2abc:def1::add 1194 udp
[other connection specific configs]
</connection>
<connection>
remote 1.2.3.4 1194 udp
[other connection specific configs]
</connection>
It’s even easier to just provide a remote hostname that resolves to IPv4 and IPv6, but as you seem to be cautious, you would “leak” this DNS lookup then.