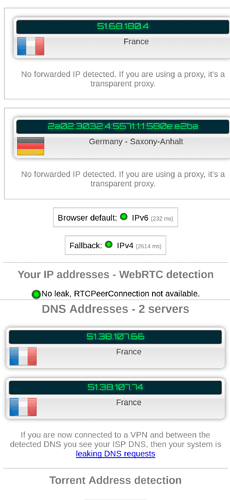
disabling IPv6 for all interfaces and setting the autoconf to 0 did not work.
After two month’s of struggling with the DNS leak I finally came close to a solution. Installing DNSCrypt.
Kudo’s to the real hero’s here @wickedsp1d3r and @kan_ibal who figured out and shared how to make DNSCrypt work on Sailfish OS.
I followed the instructions on https://together.jolla.com/question/210761/dnscrypt-on-sailfish/ and after I successfully removed any DNS leaks on a WIFI network.
I download the last linux-arm release (for my Sony Xperia XA2) from: Releases · DNSCrypt/dnscrypt-proxy · GitHub
tar -xzvf ./dnscrypt-proxy-linux_arm-{FILL_IN_YOUR_VERSION_NR}.tar.gz -C /tmp
set attribute
chmod +x /tmp/linux-arm/dnscrypt-proxy
then install dnscrypt-proxy service
/tmp/linux-arm/dnscrypt-proxy -service install
move the example-dnscrypt-proxy conf file
cp /tmp/linux-arm/dnscrypt-proxy/example-dnscrypt-proxy.toml /etc/
edit the file by adding the DNS Crypt info. (I use decloudus.com)
vi /etc/dnscrypt-proxy/dnscrypt-proxy.toml
I disabled ConnMan’s DNS proxy and override its systemd service:
- create a folder named “connman.service.d”
mkdir /etc/systemd/system/connman.service.d
- Put a file named “override.conf” to the folder with the following content using vi
[Service] ExecStart= ExecStart=/usr/sbin/connmand -n -W nl80211 --nobacktrace --systemd --noplugin=wifi --nodnsproxy $SYSCONF_ARGS $CONNMAN_ARGS
make immutable by issuing
/etc/resolv.conf chattr +i /etc/resolv.conf
from the terminal on the phone (not ssh) after a reboot (in case it does not work directly, see: Permission denied for chattr +i command - #2 by Levone1). Also applies to:
/var/run/connman/resolv.conf
and force connman to use local dnscrypt-proxy DNS address for network connections, I prefer to set it globaly, for example for all wifi connections edit
vi /home/.system/var/lib/connman/settings
and in [WiFi] section add
Nameservers=127.0.0.1;
Then I rebooted the device. And finally I got rid of the DNS leaks. It also works in combination with OpenVPN.
But when I turn off the wifi it leaked the DNS and with some trial and error now the VPN no longer connects. It tries to resolve the vpn domainname to connect and it times-out.
Two month’s in and so far I could not really circumvent this security issue. Glad though I learned about DNSCrypt and its advantages. Something I would not have looked into otherwise.