Subscribe to future posts here 
Sailfish OS update from Jolla
At the most recent community meeting there were two interesting questions related to authentication. One from lolek asking about implementing picture passwords on Sailfish OS, the other from rinigus asking about alphanumeric passwords for encrypted storage. It set my mind thinking about how Sailfish OS can help users to manage their own passwords.
Not only do we need to use passwords on our phones all the time, but our phone is also a very personal device, already contains private data, and we’re likely to have it with us more often than not. In theory, it should be the perfect device for managing passwords.
But when I started to look into it, I realised how many apps there are available for managing your passwords on Sailfish OS. Choosing the right one can be a bit of a minefield.
So in this newsletter, rather than picking out four unrelated apps to look at, we’ve scoured the Jolla Store and OpenRepos for password tools that we think might be useful. At the end you’ll find a table summarising the features of each of the tools.
If you’ve not yet chosen your preferred password management method, maybe this will help you upgrade your password approach. If you have, then please share what you do in the comments, especially if it’s one we haven’t covered here. We’re always interested to hear good ideas about how to make password management easier.
Energy from the Community
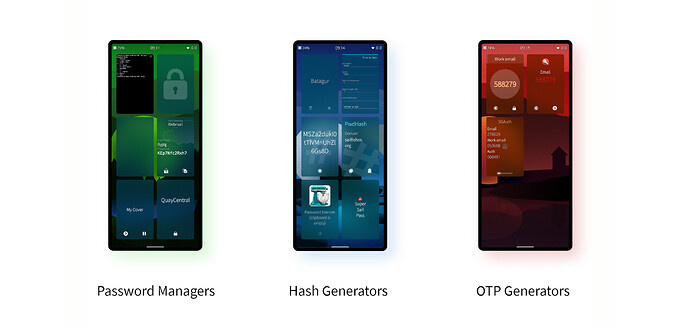
Password Managers
We all have to deal with authentication on a daily basis. Biometric, token-based and multi-factor authentication are all becoming increasingly common, but still the most widespread authentication technique in use is passwords. Password hygiene has come on leaps and bounds over the last few years. For example it’s now widely understood that using the same password across multiple accounts is bad practice, and that the torment of periodically enforced password changes does more harm than good. There’s also much more acknowledgement that using complex passwords is more important than using memorable passwords.
As a result, people are turning to password managers to help negotiate the password assault course. There are plenty of online services that will help with this, some will even ask for money to do so. But there are also plenty of free alternatives. Here we look at which are available for Sailfish OS, and which other approaches Sailfish OS has to offer.
Horses for Battery Staple Courses
To try to make sense of all the different password managers, we split the apps into three different categories: Database-, Hash- and One-Time Password- based approaches.
There are multiple apps of each type available for Sailfish OS, so let’s now dig in and take a look at each of these categories separately.
Database-based Password Managers
Probably the most common approach is to use some software that stores your passwords for you*. This database-based approach has several benefits, the most notable being that if you already have a load of accounts, you can incrementally fill up the database over time. You don’t have to change your passwords to use a tool like this, the more you use it the more benefit you get.
There are other benefits too. Some password managers will store other private data in addition to passwords. Account numbers, credit card information, answers to memorable questions, membership information. All sorts of things that you may want to keep private. If your password manager is securely storing your secret passwords, then why not this other information as well?
Some password managers will store data locally, some will store them online (“in the cloud”). Storing it online allows you to easily share it between devices. Either way, you want to be sure that they’re stored in an encrypted form to prevent prying eyes from getting access to them. If you store it online, you want to be extra certain that the encryption can’t be broken.
Encrypting the database is usually achieved with a master password. Someone with access to the database files and the master password has access to all of the passwords contained in it, so it’s important to keep the master password secret, and to use a strong master password. There are plenty of tools (including some listed here) that will tell you how strong your master password is.
pass
The pass utility is a bash script that makes use of gpg and a few other standard tools to provide secure storage of passwords. It calls itself the standard unix password manager. It’s entirely CLI-based, so you’ll need to use Fingerterm to make use of it on your phone, which isn’t entirely convenient. However, several of the other apps here use pass as their backend, which proves its versatility.
The pass tool has been packaged by shellkr and is available from OpenRepos. Unfortunately getting it to actually work isn’t entirely straightforward. Most notably it relies on various bash-isms which aren’t supported by busybox, the default Sailfish OS shell. It is possible to install gnu-bash, gnupg2 and pinentry to get it to work, but replacing the default shell isn’t recommended. If you do, you must be careful to restore busybox-symlinks-bash to return to the original state when you’re done testing.
You also have to import or generate a gpg key and initialise pass with it.
gpg2 --gen-key
gpg2 --list-secret-keys
pass init 696F86472837F81D606FDA0F07BCF007F2D4019F
Having done this you’re then in a position to add new account entries, which are essentially key (name) - value (password) pairs. You can also include / characters in the name to provide a folder structure.
[defaultuser@Xperia10-DualSIM ~]$ pass insert "Email/Work email"
created directory: '/home/defaultuser/.password-store/Email'
Enter password for Email/Work email:
Retype password for Email/Work email:
You can then list the contents of the database with the pass command, or print out a particular password using pass show.
[defaultuser@Xperia10-DualSIM ~]$ pass
Password Store
├── Calendar
├── Cloud storage
├── Credit card
├── Email
│ ├── Email
│ └── Work email
├── Mastodon
├── PC
│ └── laptop
├── Photos
└── Test
[defaultuser@Xperia10-DualSIM ~]$ pass show "Email/Work email"
super-secret-password
In the latter case, you’ll be prompted to enter your password, which is cached temporarily by gpg-agent. One other nice feature of pass is that it’s designed for the password store to be synced to a git repository, which makes it straightforward to share across multiple devices.
As a command-line tool pass is simple, has good help, and works well. However, as a mobile app using Fingerterm it’s not ideal. It’s likely to be far preferable to make use of one of the UI front-ends available.
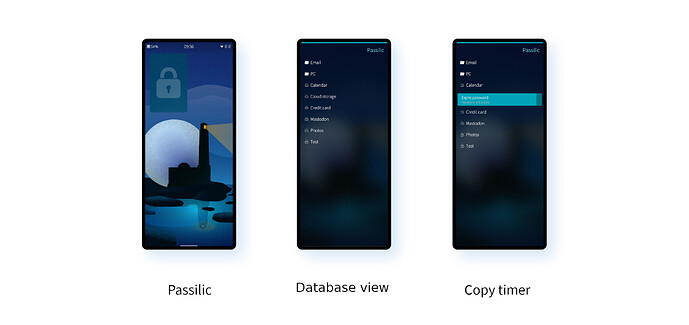
Passilic
Passilic is one of the password managers that uses pass as its backend, so you must have that installed before you can properly make use of it. Created by Daniel Vrátil (dvratil), Passilic presents a very nice, clean, user interface for pass, including the most crucial functionality of creating new entries and accessing existing entries.
I particularly like the way it shows the folder structure so nicely, and the fact that it never actually displays the passwords themselves. Instead, unlocking a password brings up a remorse timer, during which the password is stored on the clipboard. When the timer ends, the clipboard is cleared again. It’s a nice way of allowing passwords to be used in other apps via the clipboard in a relatively safe way, and it’s the only app covered here with this remorse-timer functionality.
Other than this, it’s quite straightforward. You can create new entries, where you can either enter a password yourself or get it to generate something secure for you. You can add additional notes to each entry, but you can’t edit entries created previously, or remove them.
One downside of the app is that it relies on gpg-agent to cache your password, but doesn’t provide easy control over the gpg-agent settings.
If you’re using pass as your backend database, Passilic is the most nicely designed of the options. It’s available from OpenRepos.
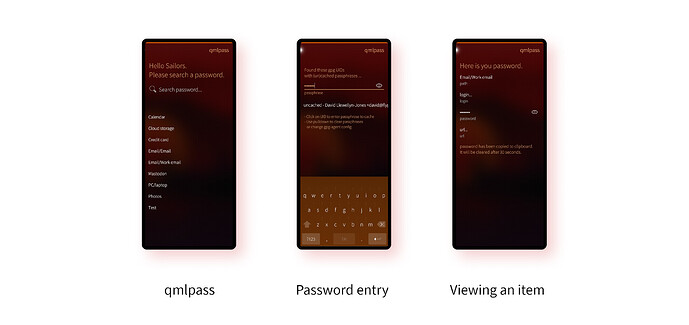
qmlpass
This is another front-end for pass, this one created by yeoldegrove and also available from OpenRepos. I found it more challenging to use than Passilic, mostly because of the way it handles password caching. First you need to “manage passphrases”, following which you can enter the password for the gpg key you want to use. It’s nice that it allows the use of different keys, but actually getting it to work required a bit of patience.
The UI for each password entry is nice, and like Passilic you can search the password list. However, it doesn’t handle folders as nicely as Passilic. You can still access values in folders, but they’re all shown in the main list. The way the pulley menus have been implemented also goes against the Sailfish style, which is a shame as it’s a small implementation detail that has a big impact on usability.
One nice feature of qmlpass is that it allows you to git pull directly from the app, so you can pull down changes synced to a git repository from another device. You can’t git push though, which is fine, because you also can’t edit or add new entries using qmlpass, it’s a strictly read-only manager.
ownKeepass
The ownKeypass app, by Marko Koschak (jobe), is probably one of the nicest UIs out of all of the database-based apps. It has nice graphics and icons and makes good use of the Silica toolkit. Unlike the previous two apps it doesn’t make use of pass as a backend; instead it makes use of a Keepass and KeepassX compatible database format.
It allows the use of multiple databases, containing folders, password entries and notes. You can add new entries, edit existing entries, remove entries and move them around. It’s a very full-featured interface. For individual entries you can either expose the password, or copy it directly to the clipboard.
Overall I was impressed by ownKeepass, and if you’re thinking of going for a database-based app, it’s definitely one to try out. It’s available from both the Jolla Store, and OpenRepos (with a separate 64-bit version).
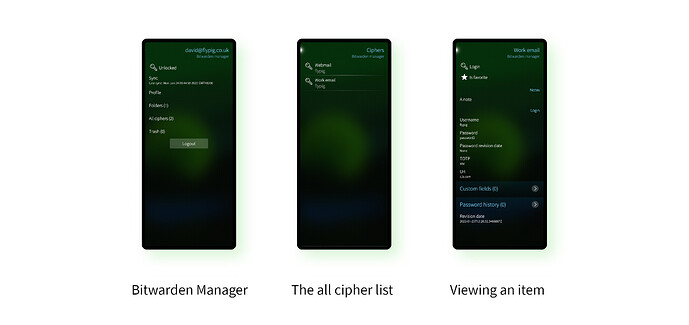
Bitwarden Manager
Bitwarden Manager is flagged by its author Vitaliy Korenev (nemishkor) as being “alpha” software. Although it has many really nice characteristics, this alpha quality does unfortunately show in some areas, most notably when getting things to initially work. Having said that, it’s also unique amongst these apps in allowing access to online Bitwarden vaults. A Bitwarden vault is available as a commercial service, or as an open-source self-hosted solution. As such, Bitwarden is a nice solution for advocates of open source.
Going back to those installation difficulties, Bitwarden Manager unfortunately relies on an old version of OpenSSL no longer supported on Sailfish OS. I wouldn’t recommend its use, but if you’re just interesting in trying Bitwarden Manager out until it gets an upgrade, you can install a version of OpenSSL which will work with it from OpenRepos.
ssu ar openrepos-lpr_A7 https://sailfish.openrepos.net/lpr_A7/personal/main
pkcon refresh
pkcon install openssl-libs10
ssu rr openrepos-lpr_A7
Even after installing this, I noted that the app refused to log in to my Bitwarden account. The reason is that Bitwarden no longer supports direct password access the way the app wants. Determined to try the software out, I hacked around this to allow the use of a client_secret instead, at which point the app worked much better. There were still some glitches, with any password entry containing empty fields crashing the app. It should be fairly easy for the author to fix these issues, but it explains why this is still considered alpha software.
Putting that to one side, the app has a nice UI and is nicely put together. You can sync your local database with your online Bitwarden vault at any time, and the password entries are laid out nicely on the page, with plenty of information shown. You can copy a password to the clipboard, however there’s no attempt to hide the passwords: they’re just shown directly when you enter the page.
While viewing entries is well supported, there’s no support for creating, editing or removing entries. Like qmlpass this is currently a strictly read-only app.
Bitwarden Manager is looking promising, and will be especially interesting for anyone already using Bitwarden, but currently it’s not in a state of real usability. It just needs a bit more time to mature in order to become truly usable. It’s available from OpenRepos.
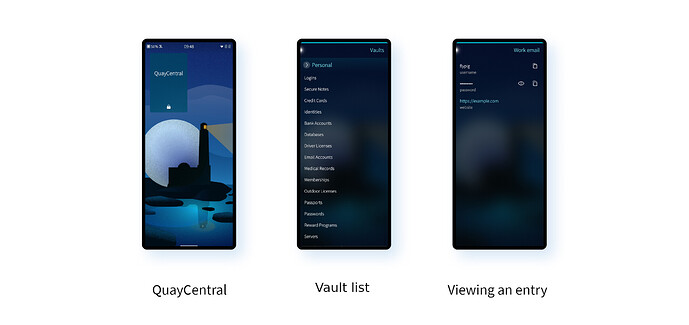
QuayCentral
QuayCentral by Michael J. Barrett (mjbdev) is the only other app here to harness an online service. In order to make use of it you’ll have to have a 1Password account. There’s no free or self-hosted version of 1Password, but it’s widely known and widely used, and many people swear by it.
QuayCentral makes use of the op command-line tool that 1Password provides. You have to install and configure this yourself before you can use QuayCentral, which makes setting up the app difficult at best. But thankfully you only have to do this once. The process I followed looked a bit like this (but you should check the OpenRepos page for links to the full instructions).
# Download, verify and install op CLI tool
curl https://cache.agilebits.com/dist/1P/op/pkg/v1.12.4/op_linux_arm_v1.12.4.zip > op_linux_arm_v1.12.4.zip
unzip op_linux_arm_v1.12.4.zip
gpg2 --keyserver keyserver.ubuntu.com --receive-keys 3FEF9748469ADBE15DA7CA80AC2D62742012EA22
gpg2 --verify op.sig op
mv op /usr/bin/op
# Create CLI shorthand login
op signin my.1password.com <my.email@address> --shorthand quaycentsfos --raw
Once it’s up and running you use your master 1Password password to access your online storage. The full structure is shown, and passwords are accessible either to view, or to be copied to the clipboard. You can search the databse or lock it at any time, after which you’ll need to enter your master password again.
However, this is another read-only tool. If you want to add, edit or remove entries, you’ll need to visit the 1Password site.
Despite the slightly painful installation process, QuayCentral is definitely the most stable and best of the two online-service apps that are covered here. It works very nicely, has a clean and usable UI, and if you’re already a 1Password user, it’ll be a really handy tool to have installed.
QuayCentral is available from OpenRepos.
Browser
It might seem a little odd to suggest the built-in Sailfish Browser as a password management app, but since it has the ability to store all your Web passwords, for some people it may be the only password manager they need.
The obvious benefit of the browser’s password manager functionality is that it’s, well, integrated into the browser. Although it is possible to send passwords to the clipboard, usually you can just let the browser fill out the relevant fields on a password entry form.
There’s no sync provided, so you can’t share passwords between devices, but you can of course add new entries, as well as edit and remove existing ones.
So although it’s not a standalone app, it’s still worth considering whether the browser already covers your needs when it comes to password management.
Hash-based Password Generators
An alternative approach to storing passwords is to use a hash-based technique for deterministically generating passwords on-the-fly. This is a neat idea, and there are many different implementations. Commonly it involves the user entering the URL of the service and their master password into their preferred hashing app. The app combined the two together, hashes the result using a one-way hash function (e.g. a PBKDF2 derivative), and uses the output from this to generate a human-readable password.
There are benefits and drawbacks to this approach too. The main benefit is that there’s no database of passwords to store anywhere. The passwords are generated directly from the master password, so as long as you can remember the master password, and have access to the app, you’re good to go. Even if you don’t have the app to hand, you can visit a website implementing the algorithm (make sure it’s a client-side and not a server-side implementation) and generate the same passwords that way. It also affords some additional protection against phishing, because the URL is also an intrinsic part of the password generation process. If a phishing site pretending to be your bank has a different URL, it’ll get a completely different password.
The main downside to the hashing approach is that you can’t generate different passwords for the same service. If your password gets compromised, or you want to change your password for some other reason, you’re out of luck. Some of the tools here try to mitigate this by allowing you to enter a password number (“this is the fourth password I’ve generated for this service”), but that increases the burden on you — the user — because it means you have to remember that number too, for each site.
The other downside of hashing approaches is that they rely on it being computationally infeasible to invert the hash. This isn’t always true in practice. Hash cracking tools are widespread and aim to do exactly this. Any service where you use a password could potentially also derive your master password. The best way to protect against this is to use a very strong master password.
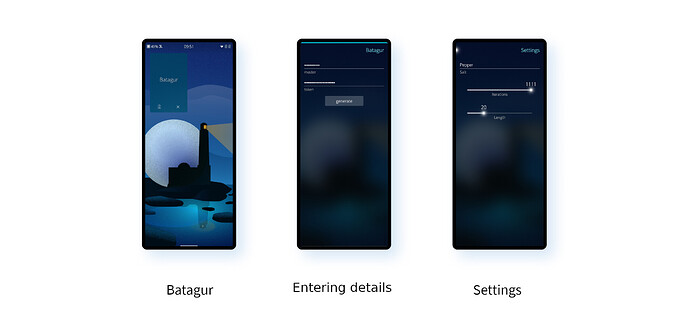
Batagur
According to Wikipedia, in the real world Batagur is a genus of turtle. But on OpenRepos you’ll find it as an app developed by toerb for deterministically generating passwords. Like most tools of this ilk you have to enter two values: a master password and the URL of a service. Batagur uses the terminology of “service token” for the latter. In addition, you can also configure a “salt” value (an additional string added to the hash of all of the passwords), as well as specifying the length of password to output, and the number of hash iterations to apply. All of these values affect the passwords to be generated, so they must be set the same on all devices you want to use the tool on.
Having generated a password, it’s displayed and you have the option to transfer it to the clipboard.
There is an online version of Batagur, but I had difficulty persuading it to generate the same values as the app.
The app is fairly bare-bones — not the most full-featured of the hashing apps we have here — and the fact the online version doesn’t match works against it. But it does the job, so if you’re already using it, it’s probably not worth replacing.
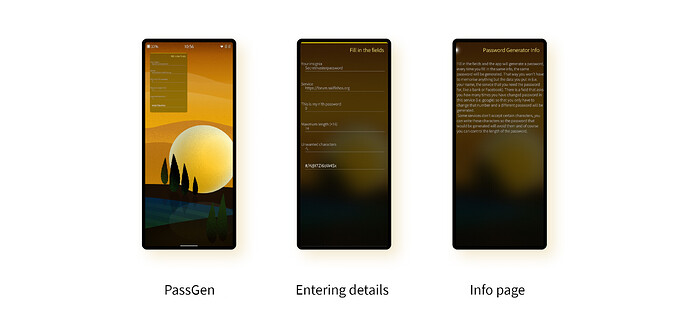
PassGen
PassGen by Orestes Kyriakos Poulakis (orestes1986) is one of the more customisable hash-based password generators. Alongside the “insignia” (which I take to be the master password) and service (the URL), you can also specify the length of password to output, a list of characters not to include in the result, and a number representing how many times you’ve generated a new password for the account.
The last one of these is useful if you want to revoke an existing password. Many of the other hash-based apps will always output the same password no matter what (to alter this, you have to change your master password), so it’s nice to have this feature. On the other hand, you, as the user must remember the correct value for each service you use.
Apart from this, it’s another rather bare-bones app. There’s no homescreen cover, and no option to send the result to the clipboard for example, although since it’s shown in a text field you can copy it yourself by highlighting it.
The link to the Web version unfortunately generates a 404 error, so it seems the service and app are no longer being maintained. However, you can get yourself a copy from both the Jolla Store and OpenRepos.
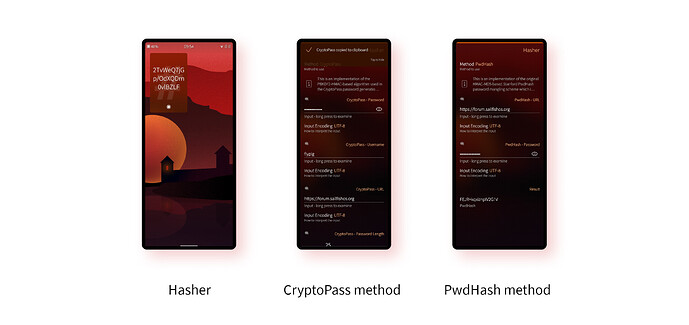
Hasher
Hasher is the most full-featured of all the hash-based apps here. That’s largely because, unlike the other apps here, it doesn’t have password-generation as its sole purpose. In fact, it’s much more of a general hashing tool that happens to be able to generate deterministic passwords as well.
The app is also very nicely designed, with little help icons scattered throughout the UI which provide additional info when clicked on. You also get a lot of configurability. For example, the Stanford PwdHash hashing algorithm is supported, which generates an output based on the length and characters of the master password used, while the CryptPass algorithm allows these characteristics to be specified separately from the master password.
In practice, users are likely to choose one of the algorithms and stick to it to avoid confusion, but it’s nice that Hasher provides much more than just password generation.
Hasher is created by Yann Büchau (nobodyinperson) and can be downloaded from OpenRepos.
PwdHash
PwdHash was originally created by Robert Gerlach, but maintenance has now been taken over by flypig who — as the author of this piece — may not be entirely unbiassed.
In essence PwdHash is very similar to the other tools covered here. Like Hasher it supports the Stanford PwdHash algorithm, but its unique feature is that it also supports the Cambridge PwdHash variant, which allows a “salt” and iterations to be configured for additional security. Apart from that, it also gives an immediate indication of your master password strength using the zxcvbn algorithm.
There are online web-based versions of both the Stanford and Cambridge versions of PwdHash in case you want to generate the same passwords on other devices.
MkPass
MkPass from Franck Routier (alci) is a free-form hash generator. It’s aimed at deterministic password generation, but in practice you have just one field to complete, and must use your own scheme (e.g. “master + URL”) to use for input to the hash function.
This minimalist approach is certainly flexible, but in day-to-day use it’s convenient to have different fields for the different elements, and have the app choose the generation approach for you. As such, MkPass wouldn’t be my first choice for daily use.
Passwords are automatically transferred to the clipboard as they’re generated, and you can clear the clipboard from the cover screen. MkPass is a simple implementation, but for frequent password generation, probably not the easiest to use amongst the ones we’re covering here.
SuperSailPass
The SuperSailPass app from Jens Clingen jklingen from the Jolla Store is an implementation of the SuperGenPass algorithm. It’s another quite simple app: add your master password and the service URL and hit generate. The password is never shown, but copied to the clipboard for 15 seconds before being removed.
You can, if you want, activate “advanced mode” which allows you to also set a “salt”, the password length and the hashing algorithm. There’s an online version available, so you can also generate the same passwords from other devices.
Passy
The last of the hash-based password generators we could find, Passy by koru is available on the Jolla Store. Like most of the others, you enter a master password and the URL (referred to here as a “key”). Then either hit enter, or the Copy button, and the generated password will be transferred to the clipboard.
It’s one of the most minimal implementations here. I wasn’t able to find an online version to use with other devices, and the passwords generated are always 26 characters long, so may not be suitable for services which restrict password length (sadly, there are still some out there). And while the UI is simple, it’s perhaps a bit too simple in this case, what with there being no homescreen cover for example.
If you’re already using Passy, there may not be a reason to change, but I’d recommend some of the other apps here in preference if you’re just starting out with hash-based password generation.
One-Time Password Generators
In addition to database-based and hashed-based tools, we’ll also look at One Time Password (OTP) tools as well. These are slightly different, since they don’t help you with your usual password chores. They’re nevertheless an important tool in the password-warrior’s armoury. Many sites (including GitHub, GitLab and many others) will allow you to activate Multi-Factor Authentication (MFA) using OTPs. You then need an app to generate tokens which periodically change (either time-based, or counter-based) and which you have to enter alongside your password when you log in. It’s an extra layer of protection.
Foil Auth
Foil Auth is part of the Foil series of apps from Slava Monich (slava). In practice what this means is that its data is stored encrypted using the same master password used for Slava’s other Foil apps. If you’re using Foil Pics or Foil Notes, then it probably makes sense to be using Foil Auth as well.
Aside from a unified password, Foil Auth also offers the usual slick interface of the other Foil apps: a very nice and useful homescreen cover, the ability to add new or edit existing tokens, and to both scan them and generate them as QR codes. Like the other OTP apps here it supports both Time-based (TOTP) and Counter-based (HOTP) One-Time Passwords.
A nice feature that’s not supported by the other apps is selection of multiple entries, allowing you to delete or share multiple entries in one go.
Foil Auth is probably the slickest out of the three OTP apps shown here, and works perfectly. It has numerous nice touches, such as the ability to automatically detect and import SailOTP tokens when run. It’s available from both the Jolla Store and OpenRepos;
SailOTP
SailOTP is very similar to Foil Auth in functionality. Unlike Foil Auth it doesn’t have a master password, so once you have access to the unlocked phone, you have access to the passwords it generates. This may be either a pro or a con depending on whether you trust your phone to be secure, and whether you have the energy to enter a master password when you use the app.
Besides this it also allows you to add, edit and remove tokens, with both TOTP and HOTP token-types supported. QR codes are supported for both import and export, and you can also import and export your tokens by file as well.
SailOTP is a very nicely written and presented app which works very well, so whether you go for Foil Auth or SailOTP will likely be a matter of preference over whether you want the token database encrypted using a master password or not.
SailOTP is available from both the Jolla Store and OpenRepos.
SGAuth
SGAuth from Andreas Storbjörk (stozze) also supports TOTP and HOTP tokens in quite a similar way to Foil Auth and SailOTP. It has similar functionality, but in practice it’s hard to recommend over the other two, mostly because the app appears to be no longer supported, and while the code is available archived on GitHub, there’s no licence specified, making it harder for someone else to pick up maintenance.
With the code not being updated, the app has unfortunately lost the ability to scan QR codes, and there are no feature for importing or exporting tokens.
Overall, while the basics are covered, unless you already have tokens stored in SGAuth, you’d be better off going with either Foil Auth or SailOTP, both of which are still being developed.
SGAuth is available from both the Jolla Store and OpenRepos.
Summary
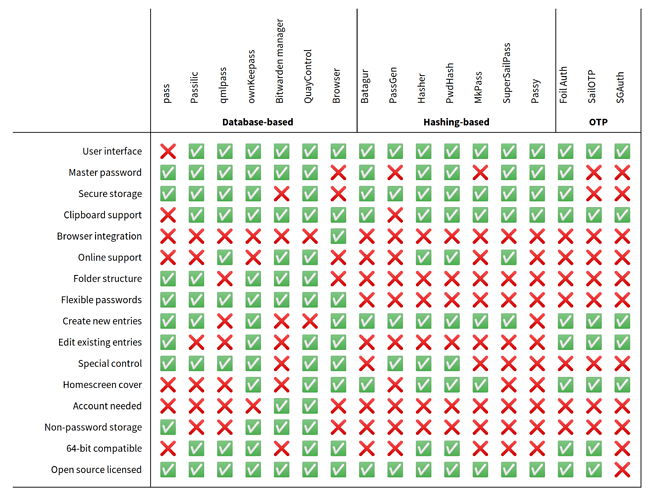
As you can see, there’s no shortage of different options for Sailfish OS. Hash-based tools and OTP tools are quite mature on Sailfish OS, largely because these tend to have fewer features than the database-based approaches.
Amongst the database-based approaches, several are built on top of pass, which is a local-storage solution. The two online-service solutions are both work-in-progresses, for example allowing reading, but not writing, of data. Hopefully they’ll improve over time.
What you use will depend on your needs, but if you’re making the decision now, hopefully this summary graph may give some ideas.
As we mentioned at the start, many of you will already have a well-established password storage mechanism for your Sailfish OS phone. We’d love to hear about them, especailly if they’re approaches not already covered here.
* Probably the most common approach is actually to “remember one password and use it everywhere”, but let’s pretend that’s not the case just for now.
Please feed us your news
This is a community update, and frankly we can’t always keep up with all the exciting stuff happening in the Sailfish community. Plus, the less of this we have to actually write ourselves the better. So please help us out by posting your Sailfish news updates to the forum as a reply to this post. We’ll collate as much of it as possible into one easily digestable post for the next update.
And don’t forget to join us at the community meeting every other Thursday on IRC. It’s a great place to discuss any of the content you see here, or to share your ideas for future updates. The next meeting will be on the 3rd February, full details here.