You could also try another ntp server instrsd of time.google.com.
Take a look at ntppool.org .
Thanx @miau I have now patched again with flag --aosp 11
Successful.
I did three reboots and got a fix indoors in around 20 seconds. That’s quite good and I usually didn’t get a fix that quickly. So i think, that AGPS is now maybe working. I will keep an eye on it.
Intresting. Using GPSinfo, how many satellites fixed/view and which horizontal precision?
You might re-enable the TLS and give a try to this patch.
It achieved 50m horizontal accuracy with 4/38 satellites fixed/view indoor. Unfortunately, the time to fix them is not very well-know because my SIM is slow to register on the 4G network. Therefore, I cannot separate the process of registering from the one used to established the position with on Earth triangulations. 
@miau I changed the ntp server to the configuration which was posted by nekron here. This speeds up things a lot. I now get indoors a fix in around 10s with the grapheneos server. Thanx for the tip to change the ntp server.
@robang74 I have after a reboot 6-7 satellites fixed (out of around 40 visible). Accuracy at the very beginning 7-8m after a short while it improves to around 4m. But you have to consider, that I live in a penthouse flat. So there is just the roof between me and the sky.
I’m happy that my config is working. This is my daily driver, so to be honest, at the moment I don’t want to tinker to much with that device. And will leave my GPS configuration like it is. If there will be a Xperia 10IV or V, I will have a testing device again, but at the moment I just tinker where I think it is necessary.
I understand your PoV.
Unfortunately, I did not find the sources to compile my own suplpatch… 
Someone have some information about this:
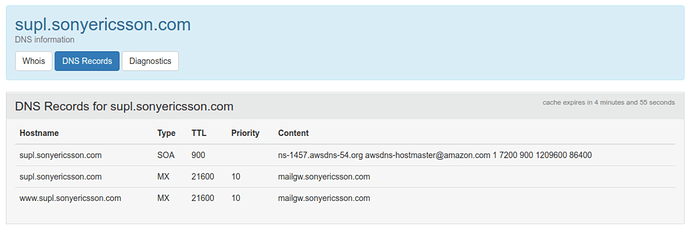
$ nslookup supl.sonyericsson.com
Server: 127.0.2.2
Address: 127.0.2.2#53
Non-authoritative answer:
*** Can't find supl.sonyericsson.com: No answer
Therefore, I go to query who.is and here you are:
This Amazon hostname can be resolved.
$ host -t ANY ns-1457.awsdns-54.org 9.9.9.9
Using domain server:
Name: 9.9.9.9
Address: 9.9.9.9#53
Aliases:
ns-1457.awsdns-54.org has address 205.251.197.177
ns-1457.awsdns-54.org has IPv6 address 2600:9000:5305:b100::1
Just for sake of completenesse, I am surf the internet from a network IPv4 only.
Yeah, it is the DNS server for this domain. It says that there is no such entry (A record) for supl.sonyericsson.com. So I guess the Sony provided SUPL service is gone.
It is not gone, yet… 
The technical problem is not a problem, but why they did that? Who knows?
Adding this line below in /etc/hosts would help?
205.251.197.177 supl.sonyericsson.com
It is risky because it can change IP but it worth a try. In fact, the 7275 port is still open and responding:
~$ telnet 205.251.197.177 7275
Trying 205.251.197.177...
Connected to 205.251.197.177.
Escape character is '^]'.
Or better it is just a matter of rename the service in gps.conf like supl.sonyericsson.com → ns-1457.awsdns-54.org, in fact:
~$ telnet ns-1457.awsdns-54.org 7275
Trying 2600:9000:5305:b100::1...
Connected to ns-1457.awsdns-54.org.
Escape character is '^]'.
That domain can be resolved and questioned at 7275 port service.
I don’t think so. Because it is an Amazon DNS-54 server. I’d be surprised if it would do SUPL services. Other than that, IIRC, it is not the phone itself which would need help with resolving that name, but the modem, which is unlikely to use your phone’s /etc/hosts file for resolving hints.
Of course, I could be totally wrong. But I have the feeling you are barking up the wrong tree. A proper, resolvable SUPL hostname has to be configured at a place where the modem’s firmware is able to read and make use of it. And that is what I’d guess the SUPL patchers do, amongst other things.
There are some reason to think that suplpatcher is obsolete by now, at least for Xperia 10 II and III. Let me explain why:
-
first of all
suplpatcheris a closed-source binary (AFAIK), therefore as long as it is a closed source binary it may arise the doubt of compromising the OS/modem/GPS and their security or privacy constrains plus the doubt that it can infringe some kind of Qualcomm exclusive right (thirdy-party reasonable doubts, not mine doubts nor my claims - expecially for a company like Jolla near the banckrupt and with some Russian ties/debt not 100% addressed, yet). -
secondly, in its easy way of doing goes against the privacy because it removes the
TLSlayer letting theSUPLrequest/answer transits uncrypted, in clear. -
it has been reported that suplpatcher CA certs uploading does not persist after a smartphone reboot or a modem hard reset (not tested by myself, just read about)
You might ask what is remain in pushing suplpatcher out of the scene. The answer is to let the Qualcomm modem/GPS to retrieve by its own the CA certs from a folder.
Like the PM2 patch above does. It does with Google SUPL services because it was straighforward to test with their service (cfr. patch description). Once, the approach is verified to be working then more SUPL providers can be added as far as they publish their CA certs in a format that Qualcomm modem/GPS can deal with.
UPDATE: about the GPS patch alternative to suplpatcher
The new v0.0.7 patch is available on Patch Manager Web Catalog.
Probably, it works also on XA2 but I did not check that its original gps.conf is the same.
Cheers, R-
About SUPL service, there is still an alternative to Google one:
~$ nslookup supl.izatcloud.net
Server: 127.0.2.2
Address: 127.0.2.2#53
Non-authoritative answer:
Name: supl.izatcloud.net
Address: 207.114.132.150
~$ telnet supl.izatcloud.net 7275
Trying 207.114.132.150...
Connected to supl.izatcloud.net.
Escape character is '^]'.
After all, we are using a Qualcomm modem/GPS and thus it seems reasonable to send to them also the SUPL requests. Moreover, the CAcerts are included into ASOP image also. Otherwise also the XTRA queries cannot be validated with the HTTPS protocol.
To restart the GPS:
- switch off the GPS by UI because I do not know the command line for this
- devel-su systemctl restart ofono
When the mobile 4G data connection is established
- switch on the GPS
Anything else?
UPDATE
Very interesting this part of GrapheneOS FAQ about GPS privacy:
On 4th and 5th generation Pixels (which use a Qualcomm baseband providing cellular, Wi-Fi, Bluetooth and GNSS in separate sandboxes), almanacs are downloaded from
which is a cache of Qualcomm’s data. Alternatively, the standard servers can be enabled in the Settings app which will use
- https://path1.xtracloud.net/xtra3Mgrbeji.bin
- https://path2.xtracloud.net/xtra3Mgrbeji.bin
- https://path3.xtracloud.net/xtra3Mgrbeji.bin
GrapheneOS improves the privacy of Qualcomm PSDS (XTRA) by removing the User-Agent header normally containing an SoC serial number (unique hardware identifier), random ID and information on the phone including manufacturer, brand and model. We also always fetch the most complete XTRA database variant (xtra3Mgrbeji.bin) instead of model/carrier/region dependent variants to avoid leaking a small amount of information based on the database variant.
Qualcomm Snapdragon SoC devices also fetch time via NTP for xtra-daemon instead of using potentially incorrect OS time. We use time.grapheneos.org when using the default GrapheneOS PSDS servers or the standard time.xtracloud.net when using Qualcomm’s servers. Stock Pixel OS uses time.google.com but we follow Qualcomm’s standard settings to match other devices and to avoid the incompatible leap second handling. These connections all go through the Owner VPN so it isn’t a real world fingerprinting issue.
Regarding suplpatcher:
- the tool was developed reverse engineering public (inofficial) sources based on Github repositories
- the tool uses the
/dev/diaginterface to send QCOM diag commands - one of these commands disables SUPL TLS so that the non-TLS based service running at port 7276 can be used to get ephemeris data. This is done by overwriting a dedicated NVRAM setting which is reboot safe.
- the same goes for the certificates injected into the SoC modem. Using the
/dev/diagdevice you can access the modems internal file system. There is a location where TLS certificates are stored and used by modem to verify SUPL TLS and XTRA endpoints (if modem fetches the XTRA data, but usually this is injected by OS).suplpatcheruploades the CA certificates used by Google and Let`s Encrypt so if you are hosting your own SUPL reverse proxy you can easily protect it by using LE. My internal tests provided the result that the SoC stored certificates are not deleted when the device was rebooted. The certs eventually will be deleted if you reflash the device using Sony Emma tool as the modems internal filesystem partition would be restored with default files (and thus the expired supl.sonicericsson.com certificate).
QCom provides QMI interface which is used by Android to talk to the modem. The proprietary Sony blobs like the gnss service are using this to talk to the GPS engine. In comparison to Android SailfishOS is still missing the function for injecting certificates via QMI or the gnss service provided by Sony. Injecting certs via suplpatcher simply is some workaround for this allowing the modem to use its internal certificates when there is no certificate injection from the operating system.
It’s an interesting idea to add the XTRA cert path for modem-internal downloading of the almanac data. Thus maybe resolves the missing cert injection issue and SUPL TLS endpoints can afterwards be used because of XTRA certs injected into modem using the XTRA_CA_PATH setting done internally by gnss service blob.
Do you think that it would be possible to store in a permanent way (reboot safe) the full global amanac for XTRA v3 into modem/GPS? Because this feature will allows us to use efficiently this parameter:
# this is modify for xtra Donwload interval
# only valid for mobile network data
# XTRA_INTERVAL = 86400
and updating the almanac every day but at least at each cold start will use a reasonable updated and complete version. What do you think about?
Do you think that cerficates upload from this folder
XTRA_CA_PATH = /system/etc/security/cacerts
will takes precious time during the cold start that can be better spent in fixing the point? In this case the most interesting certificates are about supl.izatcloud.net which is a SUPL global provider running by Qualcomm.
UPDATE
The first 15s are related to CAcerts injection and almanac update from 4G connection. This means that updating these information permantly (reboot persisten) into the modem/GPS will halve the current cold start fixing time. The best, it would be having a procedure that let the modem/GPS update these information and then send to it a store-for-ever command. Unless, the SFOS is using an initialising procedure at boot that specifically reset to the factory the modem/GPS and this would explain the misbehaviour of the XTRA_INTERVAL = 86400 parameter.
UPDATE #2
Looking for the modem firmware, I found this file
/vendor/firmware_mnt/verinfo/ver_info.txt
Searching for the modem string
MPSS.AT.4.3.1.c6-00004-NICOBAR_GEN_PACK-1
I found this Jappanse website
which enlist the specifications and among them the CAcerts pre-loaded into the firmware. This is the list:
CN=AAA Certificate Services,O=Comodo CA Limited,L=Salford,ST=Greater Manchester,C=GB
C=ES,O=ACCV,OU=PKIACCV,CN=ACCVRAIZ1
CN=Actalis Authentication Root CA,O=Actalis S.p.A./03358520967,L=Milan,C=IT
CN=AddTrust External CA Root,OU=AddTrust External TTP Network,O=AddTrust AB,C=SE
CN=AffirmTrust Commercial,O=AffirmTrust,C=US
CN=AffirmTrust Networking,O=AffirmTrust,C=US
CN=AffirmTrust Premium,O=AffirmTrust,C=US
CN=AffirmTrust Premium ECC,O=AffirmTrust,C=US
CN=Amazon Root CA 1,O=Amazon,C=US
CN=Amazon Root CA 2,O=Amazon,C=US
CN=Amazon Root CA 3,O=Amazon,C=US
CN=Amazon Root CA 4,O=Amazon,C=US
C=DE,O=Atos,CN=Atos TrustedRoot 2011
CN=Autoridad de Certificacion Firmaprofesional CIF A62634068,C=ES
CN=Baltimore CyberTrust Root,OU=CyberTrust,O=Baltimore,C=IE
CN=Buypass Class 2 Root CA,O=Buypass AS-983163327,C=NO
CN=Buypass Class 3 Root CA,O=Buypass AS-983163327,C=NO
CN=CA Disig Root R2,O=Disig a.s.,L=Bratislava,C=SK
CN=CFCA EV ROOT,O=China Financial Certification Authority,C=CN
CN=COMODO Certification Authority,O=COMODO CA Limited,L=Salford,ST=Greater Manchester,C=GB
CN=COMODO ECC Certification Authority,O=COMODO CA Limited,L=Salford,ST=Greater Manchester,C=GB
CN=COMODO RSA Certification Authority,O=COMODO CA Limited,L=Salford,ST=Greater Manchester,C=GB
CN=Certigna,O=Dhimyotis,C=FR
CN=Certigna Root CA,OU=0002 48146308100036,O=Dhimyotis,C=FR
CN=Certum Trusted Network CA,OU=Certum Certification Authority,O=Unizeto Technologies S.A.,C=PL
CN=Certum Trusted Network CA 2,OU=Certum Certification Authority,O=Unizeto Technologies S.A.,C=PL
CN=Chambers of Commerce Root - 2008,O=AC Camerfirma S.A.,2.5.4.5=#1309413832373433323837,L=Madrid (see current address at www.camerfirma.com/address),C=EU
CN=Cybertrust Global Root,O=Cybertrust\, Inc
CN=D-TRUST Root Class 3 CA 2 2009,O=D-Trust GmbH,C=DE
CN=D-TRUST Root Class 3 CA 2 EV 2009,O=D-Trust GmbH,C=DE
CN=DST Root CA X3,O=Digital Signature Trust Co.
CN=DigiCert Assured ID Root CA,OU=www.digicert.com,O=DigiCert Inc,C=US
CN=DigiCert Assured ID Root G2,OU=www.digicert.com,O=DigiCert Inc,C=US
CN=DigiCert Assured ID Root G3,OU=www.digicert.com,O=DigiCert Inc,C=US
CN=DigiCert Global Root CA,OU=www.digicert.com,O=DigiCert Inc,C=US
CN=DigiCert Global Root G2,OU=www.digicert.com,O=DigiCert Inc,C=US
CN=DigiCert Global Root G3,OU=www.digicert.com,O=DigiCert Inc,C=US
CN=DigiCert High Assurance EV Root CA,OU=www.digicert.com,O=DigiCert Inc,C=US
CN=DigiCert Trusted Root G4,OU=www.digicert.com,O=DigiCert Inc,C=US
CN=E-Tugra Certification Authority,OU=E-Tugra Sertifikasyon Merkezi,O=E-Tuğra EBG Bilişim Teknolojileri ve Hizmetleri A.Ş.,L=Ankara,C=TR
CN=EC-ACC,OU=Jerarquia Entitats de Certificacio Catalanes,OU=Vegeu https://www.catcert.net/verarrel (c)03,OU=Serveis Publics de Certificacio,O=Agencia Catalana de Certificacio (NIF Q-0801176-I),C=ES
1.2.840.113549.1.9.1=#1609706b6940736b2e6565,CN=EE Certification Centre Root CA,O=AS Sertifitseerimiskeskus,C=EE
CN=Entrust Root Certification Authority,OU=(c) 2006 Entrust\, Inc.,OU=www.entrust.net/CPS is incorporated by reference,O=Entrust\, Inc.,C=US
CN=Entrust Root Certification Authority - EC1,OU=(c) 2012 Entrust\, Inc. - for authorized use only,OU=See www.entrust.net/legal-terms,O=Entrust\, Inc.,C=US
CN=Entrust Root Certification Authority - G2,OU=(c) 2009 Entrust\, Inc. - for authorized use only,OU=See www.entrust.net/legal-terms,O=Entrust\, Inc.,C=US
CN=Entrust Root Certification Authority - G4,OU=(c) 2015 Entrust\, Inc. - for authorized use only,OU=See www.entrust.net/legal-terms,O=Entrust\, Inc.,C=US
CN=Entrust.net Certification Authority (2048),OU=(c) 1999 Entrust.net Limited,OU=www.entrust.net/CPS_2048 incorp. by ref. (limits liab.),O=Entrust.net
CN=GDCA TrustAUTH R5 ROOT,O=GUANG DONG CERTIFICATE AUTHORITY CO.\,LTD.,C=CN
CN=GTS Root R1,O=Google Trust Services LLC,C=US
CN=GTS Root R2,O=Google Trust Services LLC,C=US
CN=GTS Root R3,O=Google Trust Services LLC,C=US
CN=GTS Root R4,O=Google Trust Services LLC,C=US
CN=GeoTrust Global CA,O=GeoTrust Inc.,C=US
CN=GeoTrust Primary Certification Authority,O=GeoTrust Inc.,C=US
CN=GeoTrust Primary Certification Authority - G2,OU=(c) 2007 GeoTrust Inc. - For authorized use only,O=GeoTrust Inc.,C=US
CN=GeoTrust Primary Certification Authority - G3,OU=(c) 2008 GeoTrust Inc. - For authorized use only,O=GeoTrust Inc.,C=US
CN=GeoTrust Universal CA,O=GeoTrust Inc.,C=US
CN=GeoTrust Universal CA 2,O=GeoTrust Inc.,C=US
CN=Global Chambersign Root - 2008,O=AC Camerfirma S.A.,2.5.4.5=#1309413832373433323837,L=Madrid (see current address at www.camerfirma.com/address),C=EU
CN=GlobalSign,O=GlobalSign,OU=GlobalSign ECC Root CA - R4
CN=GlobalSign,O=GlobalSign,OU=GlobalSign ECC Root CA - R5
CN=GlobalSign,O=GlobalSign,OU=GlobalSign Root CA - R2
CN=GlobalSign,O=GlobalSign,OU=GlobalSign Root CA - R3
CN=GlobalSign,O=GlobalSign,OU=GlobalSign Root CA - R6
CN=GlobalSign Root CA,OU=Root CA,O=GlobalSign nv-sa,C=BE
CN=Go Daddy Root Certificate Authority - G2,O=GoDaddy.com\, Inc.,L=Scottsdale,ST=Arizona,C=US
CN=Hellenic Academic and Research Institutions ECC RootCA 2015,O=Hellenic Academic and Research Institutions Cert. Authority,L=Athens,C=GR
CN=Hellenic Academic and Research Institutions RootCA 2011,O=Hellenic Academic and Research Institutions Cert. Authority,C=GR
CN=Hellenic Academic and Research Institutions RootCA 2015,O=Hellenic Academic and Research Institutions Cert. Authority,L=Athens,C=GR
CN=Hongkong Post Root CA 1,O=Hongkong Post,C=HK
CN=Hongkong Post Root CA 3,O=Hongkong Post,L=Hong Kong,ST=Hong Kong,C=HK
CN=ISRG Root X1,O=Internet Security Research Group,C=US
CN=IdenTrust Commercial Root CA 1,O=IdenTrust,C=US
CN=IdenTrust Public Sector Root CA 1,O=IdenTrust,C=US
CN=Izenpe.com,O=IZENPE S.A.,C=ES
CN=LuxTrust Global Root 2,O=LuxTrust S.A.,C=LU
1.2.840.113549.1.9.1=#1610696e666f40652d737a69676e6f2e6875,CN=Microsec e-Szigno Root CA 2009,O=Microsec Ltd.,L=Budapest,C=HU
CN=NetLock Arany (Class Gold) Főtanúsítvány,OU=Tanúsítványkiadók (Certification Services),O=NetLock Kft.,L=Budapest,C=HU
CN=Network Solutions Certificate Authority,O=Network Solutions L.L.C.,C=US
CN=OISTE WISeKey Global Root GA CA,OU=OISTE Foundation Endorsed,OU=Copyright (c) 2005,O=WISeKey,C=CH
CN=OISTE WISeKey Global Root GB CA,OU=OISTE Foundation Endorsed,O=WISeKey,C=CH
CN=OISTE WISeKey Global Root GC CA,OU=OISTE Foundation Endorsed,O=WISeKey,C=CH
CN=QuoVadis Root CA 1 G3,O=QuoVadis Limited,C=BM
CN=QuoVadis Root CA 2,O=QuoVadis Limited,C=BM
CN=QuoVadis Root CA 2 G3,O=QuoVadis Limited,C=BM
CN=QuoVadis Root CA 3,O=QuoVadis Limited,C=BM
CN=QuoVadis Root CA 3 G3,O=QuoVadis Limited,C=BM
CN=QuoVadis Root Certification Authority,OU=Root Certification Authority,O=QuoVadis Limited,C=BM
CN=SSL.com EV Root Certification Authority ECC,O=SSL Corporation,L=Houston,ST=Texas,C=US
CN=SSL.com EV Root Certification Authority RSA R2,O=SSL Corporation,L=Houston,ST=Texas,C=US
CN=SSL.com Root Certification Authority ECC,O=SSL Corporation,L=Houston,ST=Texas,C=US
CN=SSL.com Root Certification Authority RSA,O=SSL Corporation,L=Houston,ST=Texas,C=US
CN=SZAFIR ROOT CA2,O=Krajowa Izba Rozliczeniowa S.A.,C=PL
CN=Secure Global CA,O=SecureTrust Corporation,C=US
CN=SecureSign RootCA11,O=Japan Certification Services\, Inc.,C=JP
CN=SecureTrust CA,O=SecureTrust Corporation,C=US
CN=Sonera Class2 CA,O=Sonera,C=FI
CN=Staat der Nederlanden EV Root CA,O=Staat der Nederlanden,C=NL
CN=Staat der Nederlanden Root CA - G2,O=Staat der Nederlanden,C=NL
CN=Staat der Nederlanden Root CA - G3,O=Staat der Nederlanden,C=NL
CN=Starfield Root Certificate Authority - G2,O=Starfield Technologies\, Inc.,L=Scottsdale,ST=Arizona,C=US
CN=Starfield Services Root Certificate Authority - G2,O=Starfield Technologies\, Inc.,L=Scottsdale,ST=Arizona,C=US
CN=SwissSign Gold CA - G2,O=SwissSign AG,C=CH
CN=SwissSign Silver CA - G2,O=SwissSign AG,C=CH
CN=T-TeleSec GlobalRoot Class 2,OU=T-Systems Trust Center,O=T-Systems Enterprise Services GmbH,C=DE
CN=T-TeleSec GlobalRoot Class 3,OU=T-Systems Trust Center,O=T-Systems Enterprise Services GmbH,C=DE
CN=TUBITAK Kamu SM SSL Kok Sertifikasi - Surum 1,OU=Kamu Sertifikasyon Merkezi - Kamu SM,O=Turkiye Bilimsel ve Teknolojik Arastirma Kurumu - TUBITAK,L=Gebze - Kocaeli,C=TR
CN=TWCA Global Root CA,OU=Root CA,O=TAIWAN-CA,C=TW
CN=TWCA Root Certification Authority,OU=Root CA,O=TAIWAN-CA,C=TW
CN=TeliaSonera Root CA v1,O=TeliaSonera
CN=TrustCor ECA-1,OU=TrustCor Certificate Authority,O=TrustCor Systems S. de R.L.,L=Panama City,ST=Panama,C=PA
CN=TrustCor RootCert CA-1,OU=TrustCor Certificate Authority,O=TrustCor Systems S. de R.L.,L=Panama City,ST=Panama,C=PA
CN=TrustCor RootCert CA-2,OU=TrustCor Certificate Authority,O=TrustCor Systems S. de R.L.,L=Panama City,ST=Panama,C=PA
CN=UCA Extended Validation Root,O=UniTrust,C=CN
CN=UCA Global G2 Root,O=UniTrust,C=CN
CN=USERTrust ECC Certification Authority,O=The USERTRUST Network,L=Jersey City,ST=New Jersey,C=US
CN=USERTrust RSA Certification Authority,O=The USERTRUST Network,L=Jersey City,ST=New Jersey,C=US
CN=VeriSign Class 3 Public Primary Certification Authority - G3,OU=(c) 1999 VeriSign\, Inc. - For authorized use only,OU=VeriSign Trust Network,O=VeriSign\, Inc.,C=US
CN=VeriSign Class 3 Public Primary Certification Authority - G4,OU=(c) 2007 VeriSign\, Inc. - For authorized use only,OU=VeriSign Trust Network,O=VeriSign\, Inc.,C=US
CN=VeriSign Class 3 Public Primary Certification Authority - G5,OU=(c) 2006 VeriSign\, Inc. - For authorized use only,OU=VeriSign Trust Network,O=VeriSign\, Inc.,C=US
CN=VeriSign Universal Root Certification Authority,OU=(c) 2008 VeriSign\, Inc. - For authorized use only,OU=VeriSign Trust Network,O=VeriSign\, Inc.,C=US
CN=XRamp Global Certification Authority,O=XRamp Security Services Inc,OU=www.xrampsecurity.com,C=US
CN=emSign ECC Root CA - C3,O=eMudhra Inc,OU=emSign PKI,C=US
CN=emSign ECC Root CA - G3,O=eMudhra Technologies Limited,OU=emSign PKI,C=IN
CN=emSign Root CA - C1,O=eMudhra Inc,OU=emSign PKI,C=US
CN=emSign Root CA - G1,O=eMudhra Technologies Limited,OU=emSign PKI,C=IN
CN=thawte Primary Root CA,OU=(c) 2006 thawte\, Inc. - For authorized use only,OU=Certification Services Division,O=thawte\, Inc.,C=US
CN=thawte Primary Root CA - G2,OU=(c) 2007 thawte\, Inc. - For authorized use only,O=thawte\, Inc.,C=US
CN=thawte Primary Root CA - G3,OU=(c) 2008 thawte\, Inc. - For authorized use only,OU=Certification Services Division,O=thawte\, Inc.,C=US
OU=certSIGN ROOT CA,O=certSIGN,C=RO
OU=ePKI Root Certification Authority,O=Chunghwa Telecom Co.\, Ltd.,C=TW
OU=Trustis FPS Root CA,O=Trustis Limited,C=GB
OU=Starfield Class 2 Certification Authority,O=Starfield Technologies\, Inc.,C=US
OU=Security Communication RootCA1,O=SECOM Trust.net,C=JP
OU=AC RAIZ FNMT-RCM,O=FNMT-RCM,C=ES
OU=Security Communication RootCA2,O=SECOM Trust Systems CO.\,LTD.,C=JP
OU=Go Daddy Class 2 Certification Authority,O=The Go Daddy Group\, Inc.,C=US
O=Government Root Certification Authority,C=TW
Another relevant information is that the modem/GPS does not change its behaviour in energy mode saving.
Position function behavior during power saving
Position function operation during power saving * NO_CHANGE
Therefore, the energy saving mode can be always kept active without influencing the GPS.
UPDATE #3
Futher research brings me to find this page in which a set of firmware are listed to be sold:
Thanks to this page, I reach the Sony Open Devices program page and found the last open source firmware package:
In particular this one:
Which contains two folder with similar content:
- seine-1.2.0-docomo
- seine-1.2.0-docomo-qssi
Someone can explain me the difference between the two?
UPDATE #4
Only source code apart these two images:
seine-1.2.0-docomo-qssi/packages/modules/BootPrebuilt/
5.4/arm64/boot-userdebug.img5.10/arm64/boot-userdebug.img
but nothing about binary firmware useful for an upgrade of the modem/GPS.
I released the v0.1.1 of the A-GPS patch which is an alternative of v0.1.0:
- the v0.1.0 is as much as possible near to the modem/GPS standard settings with IPv4
- the v0.1.1 is based on v0.1.0 but enables as many features as possible
The link is here
Both avoid the XTRA_INTERVAL = 86400 because it does not behave like I expected and thus makes the patch fail to achieve consistent results. Both do not throttle the XSTRA modem/GPS engine because energy optimisation will came later.
Give them a try and tell me which one in your case it is working at the best.
UPDATE
The v0.1.15 has been released and it will be the base for future releases.
Soooo, just posting this for letting people envy me 
Xperia XA2 single sim here
I just have the offline gps selected, with the location pack downloaded from the store
Yesterday i’ve got a fix (cold boot one) in 15 seconds, and today i’m having fixes also inside my house (of course mostly near windows but still)
Went into the garden and had a look at satellites, it was connected to almost every single satellite it could have some signal
Kinda incredible as gps always worked for me but always was an hit or miss
I wish not to ruin your day but the A-GPS patch v0.1.5 installed and doing this
~]# /odm/bin/sony-modem-switcher
~]# sleep 1
~]# /odm/bin/sony-modem-switcher
The fix is immediate indoor 5/35 under 30m of accuracy but I need to test it more… 
UPDATE
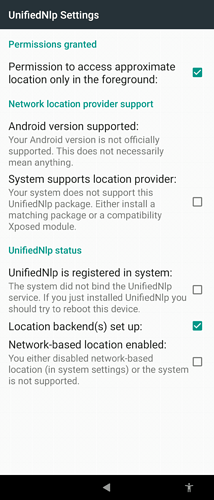
On Xperia 10 II with 4.5.0.19, about GPS only the “device mode only” works. In fact, trying to use the complementary services based on MLS, there is no hope to have a resolution better than 9000m. Moreover, the UnifiedNlp is available for Android and it is not working in full or neighter at all if we exclude the cell identification probably carried on from the GSM line.
The UnifiedNlp and the related microG software stack is a 3rd party component. I am not aware (yet) about what’s available on the native platform for offering the same service.
UPDATE #2
I confirm that a single shot of /odm/bin/sony-modem-switcher by root fix the point immediately also in device mode only.
Possibly, because I have the data
SIMon slot #2 and theofonobinder expect on the slot #1 by default. I need to investigate more about this.
Nope, the order of the SIMs does not matter but sony-modem-switcher which seems able to fix also my problem in registration my italian SIM with the network.
As far as I see, sony-modem-switcher should be triggered each time the GPS goes up the first time (cold start) or after a while (demi-cold start or fresh start) and when a SIM starts a network searching. However, coincidences does not implies cause-effect relationship.
After having tested GPS on several XA2 DUAL and XA2 SINGLE, I I seemed to remark that SINGLE ones work much better, gps wise.
I said “i have an xa2” …
Has somebody tried setting these two parameters in /etc/gps.conf? You have to reboot the phone after that. Keep in mind that the first row is already set to 0 and you only have to change it, the second row have to be added, but can be found with value 5000 in the comments in the file:
INTERMEDIATE_POS=1
ACCURACY_THRES=0
When I set these and in Settings > Location choose some mode that includes GPS position (no matter which, e.g. High accuracy) I immediately get not precise, but good enough position (indoors also), and looks like this also helps for a faster precise fix when there’re visible satellites.
I have two phones, XA2 and XA2 Plus, and I haven’t seen so fast positioning on either of them for years. If some of these matter, XA2 Plus is with Sailfish OS 4.6.0.13, XA2 is with 4.5.0.19 (long story why), both have MLS Manager from OpenRepos, and both of them have the suplpatcher from @nekron (for which I’m very thankful, but never gave me so fast fix) executed with “-disabled” flag and these additional settings in /etc/gps.conf:
NTP_SERVER = time.google.com
SUPL_HOST=supl.google.com
SUPL_PORT=7276
SUPL_VER=0x20000
I’m still not sure if the magical two parameters will lead to bigger battery consumption. And I wonder if this can help on different phone models, or also on XA2-series phones with different settings about suplpatcher, MLS database or whatever.
Edit: OK, looks like with GPS only (without MLS) getting a position after cold reboot is also blistering fast, but can be very inaccurate (I saw 180 km offset in my tests), so you need MLS database and to choose “High accuracy” in Settings. But it’s still far more precise than “MLS only” even indoors.