REPRODUCIBILITY (% or how often): Discovered once
BUILD ID = OS VERSION (Settings > About product): 4.1.0.24
HARDWARE (XA2, X10, X10 II, …): X10 II
UI LANGUAGE: German
REGRESSION: (compared to previous public release: Yes, No, ?): Unknown
DESCRIPTION:
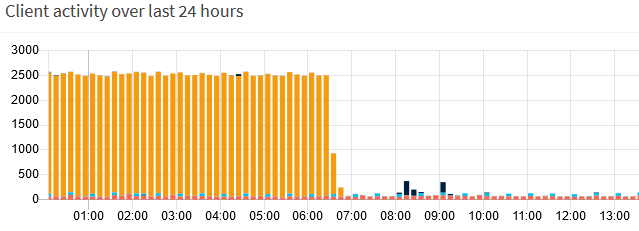
In Pi-hole, I see DNS requsts to 0.sailfishos.pool.ntp.org, about 2500 times per hour.
NTP deamon is stuck and tries to connect server over and over again!
PRECONDITIONS:
Unknown, but Wifi was active, UI inactive over night.
STEPS TO REPRODUCE:
Unkown
EXPECTED RESULT:
Time demon should try only once a while. If a network problem exists it should not act like an DoS attack. Maybe server was down, but this should not leed to such a requst flooding.
ADDITIONAL INFORMATION:
Orange graph shows activity of Sailfish phone from last night:
Are you actually answering the DNS requests with a valid IP? Or blocking them?
Are you allowing NTP both ways?
Do you see requests for the other pool timeservers (1,2,3) as well?
Also, I wouldn’t call that a DDOS, 2500 requests per hour is about 2 per second.
I briefly looked at connman source, which does the NTP on SFOS, and it should move on to the next server if lookup for the first fails.
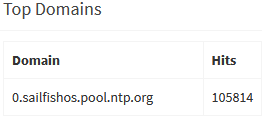
It was shown as top permitted domain. It is not blocked! Domains 1. was requested 14 times, 2. two times in the last two days, but not in the time range where the 0. loop occured.
I saw this phenomenon the first time yesterday, but now I will have an eye on it now.
How often is time synchronized normaly?
This is the requst count for last 7 days, so it hapens more than once:
The following is just from me very briefly skimming the relevant source code bits, so take it with a grain of salt:
I think connman does proper NTP, so time is not synchronized in regular intervals, but “continuously” per the NTP protocol.
Thing is, if your DHCP server deals out an NTP server, it should use that one, it only falls back to the X.sailfishos.pool.ntp.org servers if DHCP does not specify one.
It then does a DNS lookup for the first ntpserver in the list, and if it can’t resolve it, moves on to the next.
So if it does lots of lookups for 0.s.p.n.o, IMO that means:
- no NTP server information in dhcp
- the network on the device going up and down a lot (because that would initiate a lookup each time it goes up)
- resolving OR connecting to 0.s.p.n.o fails, causing lots of retries
- some other error

