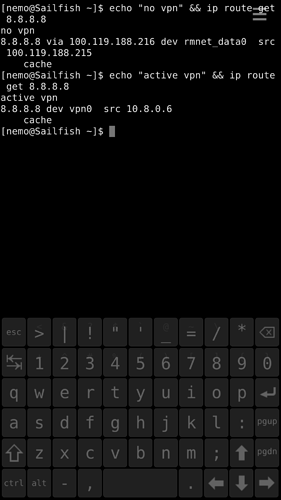
Some releases ago we got the option to enable VPN even if no network connection was enabled at the time (mobile/WLAN). VPN would then kick it right when a connection does come available, so you’re always safe if you’re using VPN as default route.
Recently I’ve been in a hotel, which only had unencrypted WLAN. No problem, VPN enabled before connecting, I’m even connecting to a direct IP instead of (my personal) dns name, so I wouldn’t leak anything other info than “there’s a connection between this device and some server on that IP-address”, so I’m good, right? Turns out, in the time between the activation of the network connection and establishment of VPN, the connection is used for all internet traffic. And thus my privacy is greatly reduced, as the e-mail client undoubtedly immediately connected to the IMAP server on my domain name right after the connection became available. While of course the IMAP connection is encrypted by itself, it could still have leaked domain names. That might have been the case for other types of accounts as well.
Not sure if this an actual bug, but I had expected all traffic to be blocked until the VPN-connection became available. Shouldn’t that be the case?